Summary
This post on Cybersecurity is 1 of 3 issues that US onAir curators are focusing on in the National Security category.
The Cybersecurity and Infrastructure Security Agency (CISA) is a component of the United States Department of Homeland Security (DHS) responsible for cybersecurity and infrastructure protection across all levels of government, coordinating cybersecurity programs with U.S. states, and improving the government’s cybersecurity protections against private and nation-state hackers.
OnAir Post: Cybersecurity
News
A cyberattack on a little-known health care company in February has caused major trouble and serious financial consequences for hospitals, doctors and patients around the United States. Stephanie Sy spoke with Dan Diamond, who has been covering the story for The Washington Post, to learn more about the impact and efforts to solve these problems.
About
Check the National Security post for the party positions, committees, government agencies related to Cybersecurity issues.
Challenges
Evolving Threat Landscape:
- Rapidly evolving cyber threats, including ransomware, phishing attacks, and zero-day vulnerabilities
2. Fragmented and Complex Cybersecurity Landscape:
- Lack of coordination and collaboration among government agencies, private sector entities, and individuals in addressing cyber threats
3. Shortage of Skilled Cybersecurity Professionals:
- Critical shortage of qualified cybersecurity experts to detect, respond to, and mitigate cyber incidents
4. Cybercrime as a Global Threat:
- Cybercrime is a transnational issue, making it challenging to attribute and prosecute perpetrators
5. Privacy and Civil Liberties Concerns:
- Cybersecurity measures can raise concerns about the protection of individual privacy and civil liberties
6. Lack of Comprehensive and Effective Legislation:
- Fragmented regulatory framework and a lack of cohesive policies to address emerging cybersecurity threats
7. Outdated Cybersecurity Infrastructure:
- Many critical infrastructure systems and government networks are vulnerable due to outdated technology and lack of investment in modernization
8. Insider Threats:
- Malicious insiders or negligent employees can compromise cybersecurity systems and data
9. International Cooperation and Diplomacy:
- Difficulty in fostering international cooperation and agreement on cybersecurity standards and best practices
10. Psychological and Social Aspects:
- Human error and poor security practices by individuals and organizations contribute to vulnerabilities in cybersecurity systems
Source: Google Search + Gemini + onAir curation
Solutions
Enhance Information Sharing and Collaboration:
- Establish a comprehensive national cybersecurity information sharing framework that connects government agencies, private sector organizations, and individuals.
- Foster partnerships between law enforcement, intelligence agencies, and industry to combat cybercrime and prevent threats.
2. Develop and Implement Robust Cybersecurity Standards:
- Establish clear and enforceable cybersecurity standards for critical infrastructure sectors, including power grids, healthcare systems, and financial institutions.
- Enforce compliance with these standards through regular audits and penalties for non-compliance.
3. Invest in Cybersecurity Education and Workforce Development:
- Increase funding for cybersecurity education programs to train a skilled workforce.
- Develop apprenticeship programs and certification initiatives to attract and retain cybersecurity professionals.
- Promote cybersecurity awareness among the general public to improve defensive practices.
4. Modernize Cybersecurity Infrastructure:
- Upgrade government cybersecurity systems to defend against evolving threats.
- Promote the use of advanced technologies, such as artificial intelligence and machine learning, to detect and respond to cyberattacks.
- Invest in research and development of innovative cybersecurity solutions.
5. Strengthen Cybersecurity Legislation and Enforcement:
- Enact comprehensive cybersecurity legislation that clarifies responsibilities, establishes penalties for cybercrimes, and enhances government powers to investigate and prosecute cybercriminals.
- Increase resources for law enforcement agencies to investigate and prosecute cybercrimes effectively.
6. Promote International Cooperation:
- Collaborate with international partners to combat cross-border cyber threats.
- Share intelligence and best practices to enhance global cybersecurity.
- Develop international agreements to deter cyberattacks and hold perpetrators accountable.
7. Strengthen Critical Infrastructure Protection:
- Protect critical infrastructure assets from cyberattacks by implementing robust security measures, redundancies, and backup systems.
- Establish plans for incident response and recovery to minimize the impact of cyberattacks.
8. Address Social Engineering and Phishing Attacks:
- Educate employees and the public about social engineering and phishing techniques.
- Develop tools and technologies to detect and block phishing emails and websites.
- Implement multi-factor authentication and other measures to strengthen user identification and access controls.
9. Promote Cloud Security and Data Protection:
- Develop best practices for cloud security and data protection.
- Encourage cloud providers to adopt rigorous security measures and comply with industry standards.
- Implement encryption and other data protection technologies to safeguard sensitive information.
10. Foster Innovation and Public-Private Partnerships:
- Support startups and small businesses that develop innovative cybersecurity solutions.
- Encourage public-private partnerships to share knowledge, resources, and expertise in addressing cybersecurity challenges.
- Promote collaboration between academia, industry, and government to advance cybersecurity research and development.
Source: Google Search + Gemini + onAir curation
Websites
Government Agencies:
- Cybersecurity and Infrastructure Security Agency (CISA): https://www.cisa.gov/
- National Security Agency (NSA): https://www.nsa.gov/
- Department of Homeland Security (DHS): https://www.dhs.gov/cybersecurity
- Federal Bureau of Investigation (FBI): https://www.fbi.gov/investigate/cyber
Nonprofit Organizations:
- Center for Internet Security (CIS): https://www.cisecurity.org/
- Information Security Forum (ISF): https://www.securityforum.org/
- National Cyber Security Alliance (NCSA): https://staysafeonline.org/
- Open Web Application Security Project (OWASP): https://owasp.org/
Industry Resources:
- NIST Cybersecurity Framework (National Institute of Standards and Technology): https://www.nist.gov/cybersecurity/cybersecurity-framework
- ISACA (Information Systems Audit and Control Association): https://www.isaca.org/
- CERT Coordination Center (Carnegie Mellon University): https://cert.org/
- MITRE ATT&CK Framework: https://attack.mitre.org/
Educational Resources:
- Cybersecurity and Infrastructure Security Agency (CISA) Training Academy: https://www.cisa.gov/training-academy
- SANS Institute: https://www.sans.org/
- Information Security Education and Awareness (ISEA): https://isea.edu/
- Coursera Cybersecurity Courses: https://www.coursera.org/browse/cybersecurity
Additional Resources:
- National Cybersecurity Awareness Month (NCSAM): https://staysafeonline.org/ncsam/
- Cybersecurity Awareness Alliance (C2SA): https://www.cybersecurityawareness.org/
- Federal Information Security Modernization Act (FISMA): https://www.nist.gov/cybersecurity/fisma-federal-information-security-modernization-act
- International Telecommunication Union (ITU) Global Cybersecurity Index: https://www.itu.int/en/ITU-D/Cybersecurity/Pages/global-cybersecurity-index.aspx
Source: Google Search + Gemini + onAir curation
Legislation
See Congress.Gov links below for latest updates and for learning what bills your representatives are sponsoring.
Laws
Source: Google Search + Gemini + onAir curation
Patriot Act (2001)
- Enhanced government surveillance and information sharing to combat terrorism
- Created the National Cybersecurity Telecommunications Integration Center (NCTIC) to coordinate cybersecurity efforts
Cybersecurity Information Sharing Act (CISA) (2015)
- Facilitates information sharing between private sector entities and the government
- Protects data shared for cybersecurity purposes from liability
National Cybersecurity and Critical Infrastructure Protection Act (NCCIP) (2013)
- Established the Cybersecurity and Infrastructure Security Agency (CISA) as a central hub for cybersecurity coordination
- Expanded the role of the Department of Homeland Security (DHS) in cybersecurity
Cybersecurity Enhancement Act (2014)
- Enhanced cybersecurity protections for federal agencies
- Established the National Cybersecurity and Communications Integration Center (NCCIC) within CISA
NIST Cybersecurity Framework (2014)
- Voluntary framework for organizations to develop and implement cybersecurity programs
- Provides guidance on risk management, threat detection, and incident response
Federal Information Security Modernization Act (FISMA) (2014)
- Modernized cybersecurity requirements for federal agencies
- Required agencies to implement continuous monitoring and vulnerability management
National Cybersecurity Strategy and Implementation Plan (2013)
- Outlined a comprehensive strategy for addressing cybersecurity challenges
- Identified five key cybersecurity goals, including protecting critical infrastructure and enhancing information sharing
Cybersecurity Act of 2021
- Comprehensive legislation to strengthen cybersecurity across the federal government
- Includes measures to enhance cyber incident reporting, improve data sharing, and expand the workforce
Quantum Computing Cybersecurity Preparedness Act (2022)
- Authorizes research and development on cybersecurity technologies to address evolving threats from quantum computing
New Bills in 2023-2024
Source: Google Search + Gemini + onAir curation
Cybersecurity Enhancement Act of 2023 (S. 2546)
- Establishes a Cybersecurity National Action Plan to coordinate federal cybersecurity efforts.
- Strengthens cybersecurity requirements for critical infrastructure.
- Creates a National Cyber Incident Response Team to enhance collaboration during cyberattacks.
2. Federal Cybersecurity Risk Management Act of 2023 (H.R. 3648)
- Requires federal agencies to implement risk management programs for their cyber assets.
- Establishes performance measures and reporting requirements for cybersecurity initiatives.
- Provides funding for cybersecurity training and workforce development.
3. Internet of Things (IoT) Cybersecurity Improvement Act of 2023 (S. 3238)
- Sets minimum cybersecurity standards for IoT devices used by federal agencies.
- Requires manufacturers to provide security labels and disclose vulnerabilities.
- Establishes a voluntary labeling program for IoT devices used by consumers.
4. Cyber Workforce Capacity Act of 2023 (H.R. 4647)
- Provides funding for cybersecurity education and training programs.
- Creates a Cybersecurity Career Pathway to attract and retain qualified professionals.
- Encourages collaboration between government, industry, and academia to strengthen the cybersecurity workforce.
5. SolarWinds Incident Response Act of 2023 (S. 2552)
- Mandates reporting of significant cybersecurity incidents by federal agencies and contractors.
- Establishes a task force to investigate the SolarWinds supply chain attack.
- Provides funding for cybersecurity research and development.
6. National Cyber Defense Protection Act of 2023 (H.R. 4323)
- Establishes a national cyber defense system to protect critical infrastructure from cyberattacks.
- Creates a cyber response fund to support recovery efforts.
- Authorizes funding for cybersecurity research and development.
7. Cybersecurity Information Sharing Act of 2024 (H.R. 8423)
- Facilitates information sharing between the public and private sectors on cybersecurity threats.
- Protects businesses from liability for sharing cybersecurity information.
- Establishes a process for reviewing and addressing cybersecurity vulnerability disclosures.
8. National Cyber Strategy Reauthorization Act of 2024 (S. 3458)
- Reauthorizes the National Cyber Strategy, providing a framework for national cybersecurity efforts.
- Updates the strategy to address emerging cybersecurity challenges, such as artificial intelligence and cyber espionage.
- Establishes performance measures and reporting requirements for the strategy’s implementation.
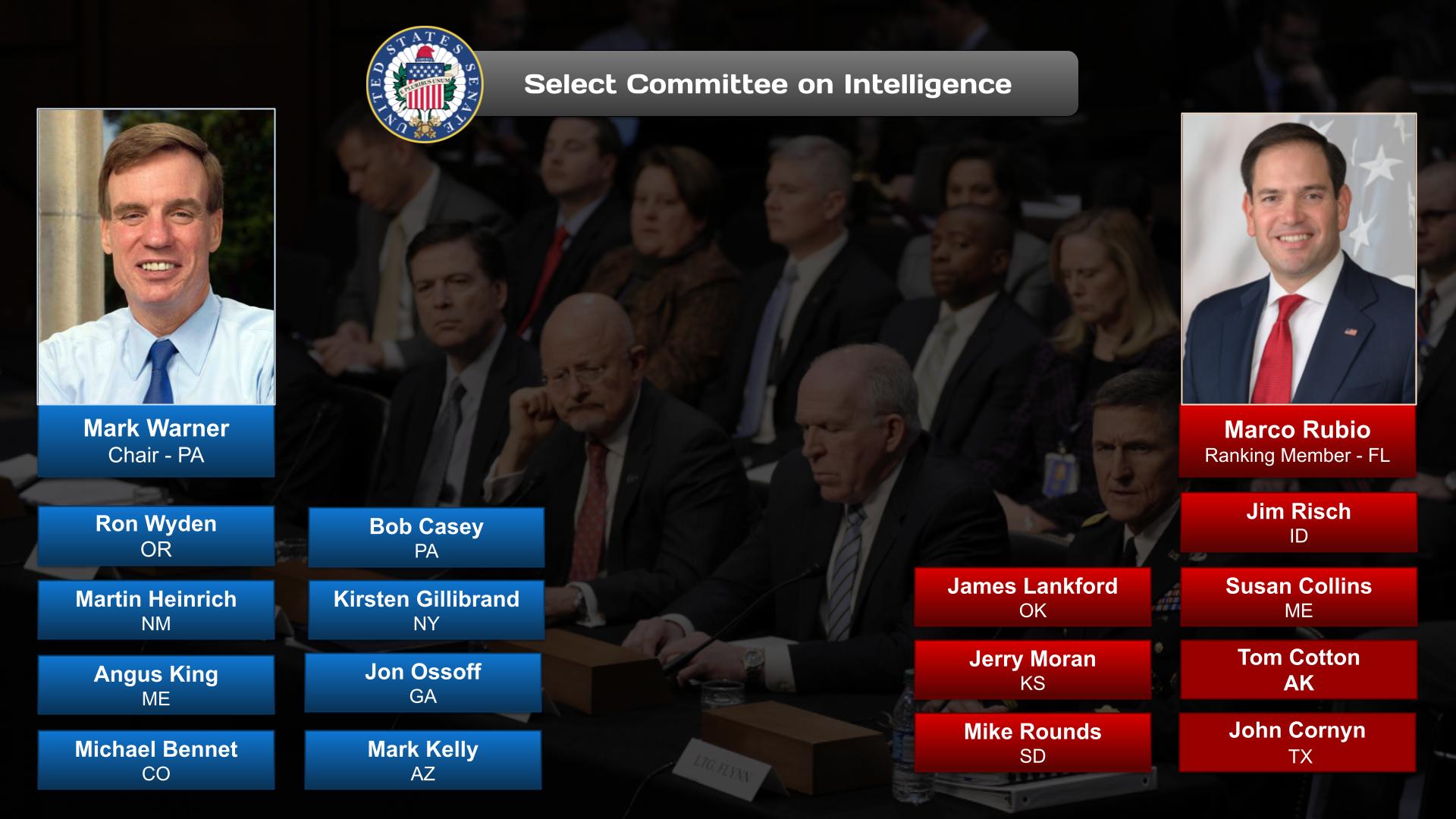
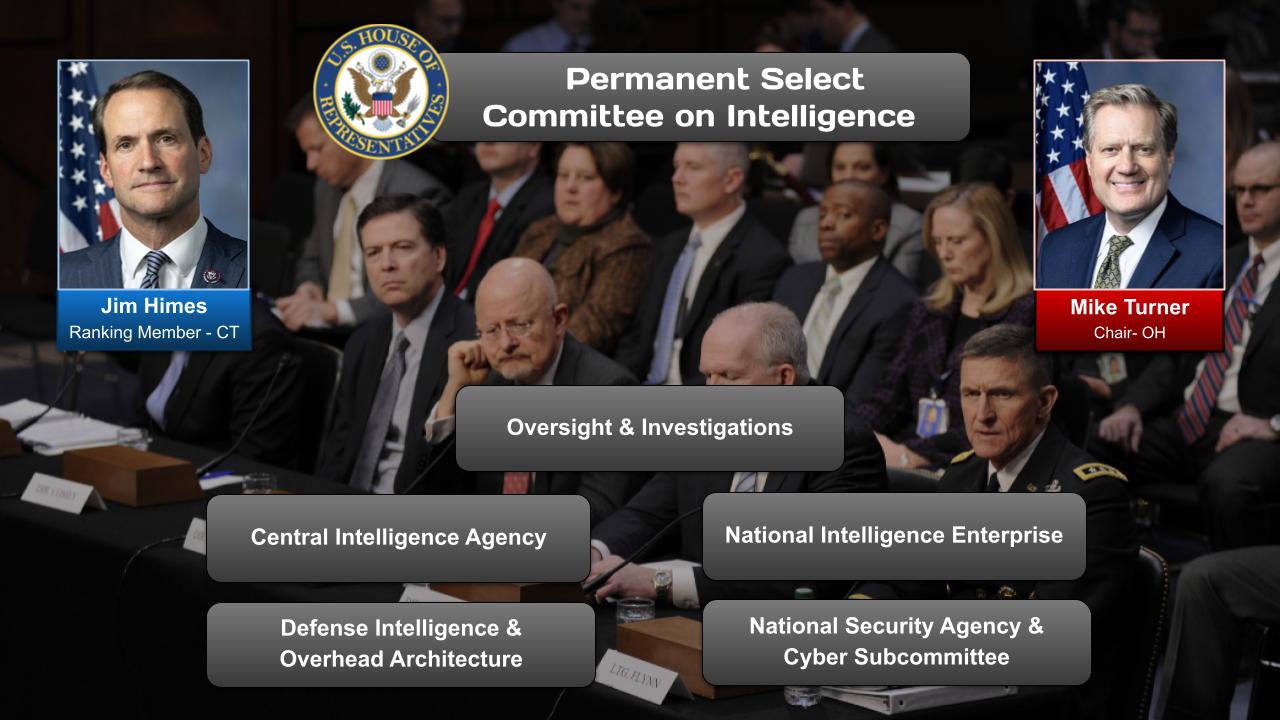
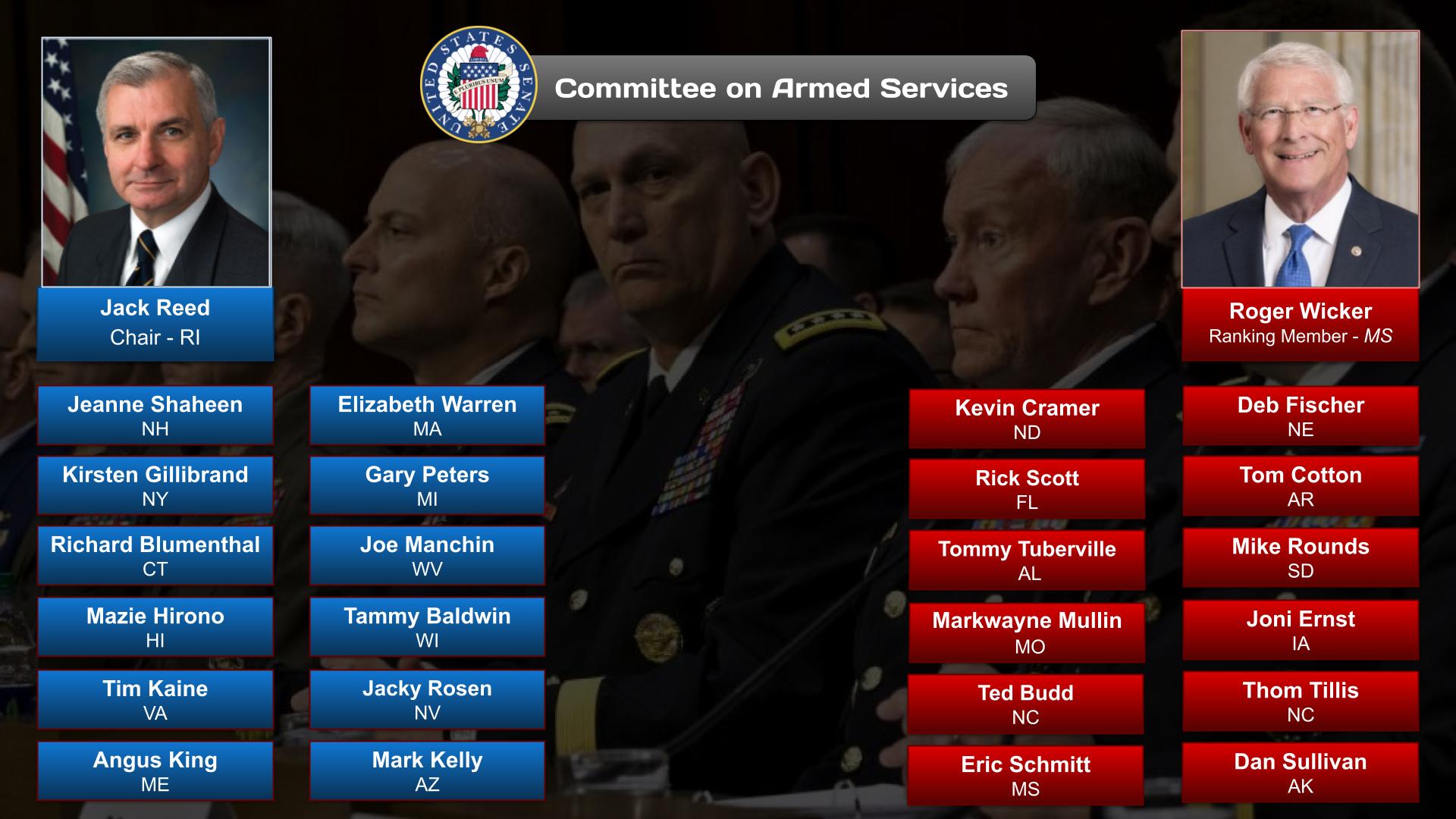
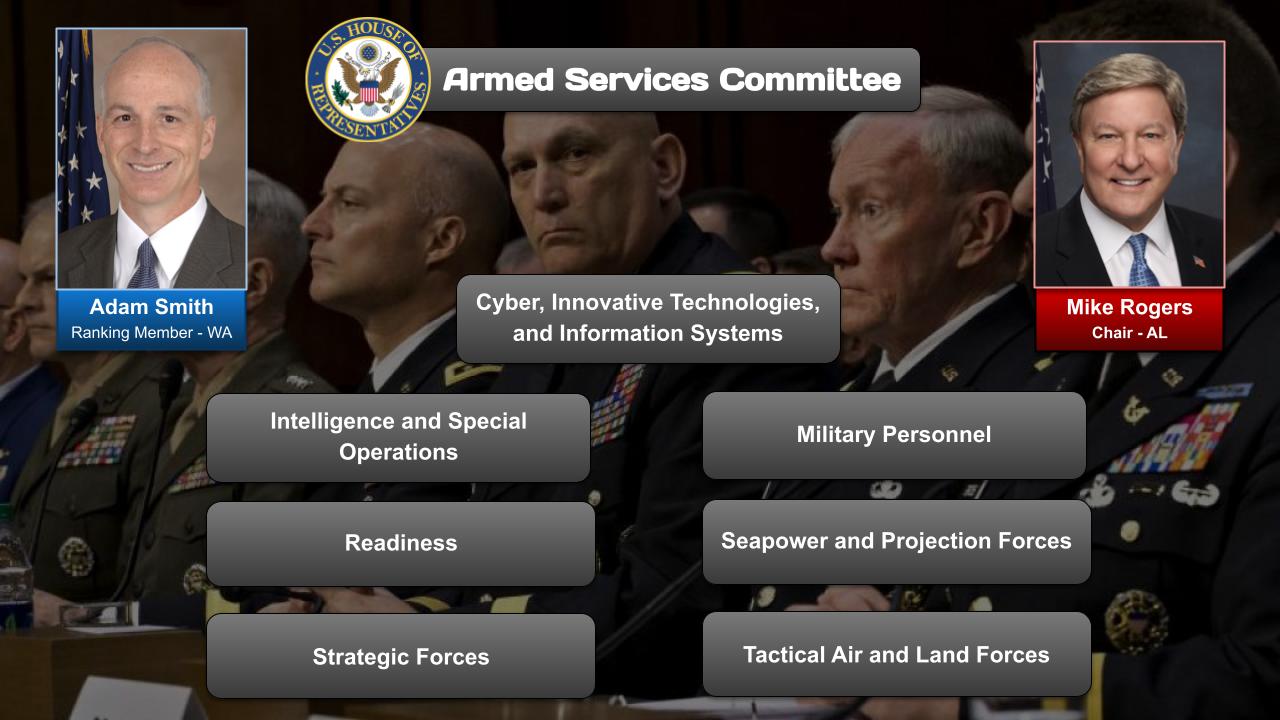
Committees, Agencies, & Programs
Committees
Source: Google Search + Gemini + onAir curation
House of Representatives
- House Committee on Homeland Security
- Subcommittee on Cybersecurity, Infrastructure Protection, and Security Technologies
- House Committee on Energy and Commerce
- Subcommittee on Communications and Technology
- House Committee on Armed Services
- Subcommittee on Cyber, Innovative Technologies, and Information Systems
Senate
- Senate Committee on Homeland Security and Governmental Affairs
- Subcommittee on Government Operations and Minority Health
- Subcommittee on Emerging Threats and Cybersecurity
- Senate Committee on Commerce, Science, and Transportation
- Subcommittee on Communications, Technology, Innovation, and the Internet
- Senate Committee on Armed Services
- Subcommittee on Cyber and Emerging Threats
Joint Committees
- Joint Select Committee on Cybersecurity (2019-2020)
Other Relevant Committees
- House Committee on Appropriations
- Subcommittee on Homeland Security
- Senate Committee on Appropriations
- Subcommittee on Homeland Security
- House Committee on the Judiciary
- Subcommittee on Privacy and Civil Liberties
- Senate Committee on the Judiciary
- Subcommittee on Privacy, Technology, and the Law
- House Committee on Science, Space, and Technology
- Subcommittee on Research and Technology
- Senate Committee on the Environment and Public Works
- Subcommittee on Water and Wildlife
Leadership Roles
- House Homeland Security Committee Chair: Mark Green (R-TN)
- House Energy and Commerce Committee Chair: Frank Pallone (D-NJ)
- House Armed Services Committee Chair: Adam Smith (D-WA)
- Senate Homeland Security and Governmental Affairs Committee Chair: Gary Peters (D-MI)
- Senate Commerce, Science, and Transportation Committee Chair: Maria Cantwell (D-WA)
- Senate Armed Services Committee Chair: Jack Reed (D-RI)
Government Agencies
Source: Google Search + Gemini + onAir curation
- Cybersecurity and Infrastructure Security Agency (CISA): CISA is the lead federal agency for cybersecurity, and it plays a vital role in protecting the nation’s critical infrastructure from cyber threats. CISA provides a range of services to businesses and government agencies, including threat intelligence, vulnerability assessments, and incident response assistance.
- Federal Bureau of Investigation (FBI): The FBI investigates cyber crimes and works to disrupt cyber threats. The FBI also provides a range of resources to businesses and individuals, including information on how to prevent cyber attacks and how to report cyber crimes.
- National Security Agency (NSA): The NSA is responsible for protecting the nation’s communications systems from cyber threats. The NSA also provides a range of services to the US government, including intelligence gathering and analysis, and cryptographic support.
- Department of Defense (DoD): The DoD is responsible for protecting the nation’s military systems from cyber threats. The DoD also works with other government agencies to develop and implement cybersecurity policies.
- Department of Homeland Security (DHS): DHS is responsible for protecting the nation’s physical and cyber infrastructure from terrorism and other threats. DHS works with a range of other government agencies to develop and implement cybersecurity policies.
Programs & Initiatives
Source: Google Search + Gemini + onAir curation
Federal Agencies
- Department of Homeland Security (DHS):
- Cybersecurity and Infrastructure Security Agency (CISA): Leads federal cybersecurity efforts, protects critical infrastructure, and provides cybersecurity resources and guidance.
- National Cybersecurity and Communications Integration Center (NCCIC): Provides real-time cybersecurity information sharing and incident response coordination.
- Department of Justice (DOJ):
- Federal Bureau of Investigation (FBI): Investigates and prosecutes cybercrimes, including hacking, malware distribution, and data breaches.
- Department of Defense (DoD):
- United States Cyber Command (USCYBERCOM): Responsible for military cybersecurity operations, including defensive and offensive measures.
- Defense Information Systems Agency (DISA): Provides cybersecurity services and infrastructure for the DoD.
Programs and Initiatives
- National Cybersecurity Strategy and Implementation Plan (NCSP): Outlines the federal government’s comprehensive approach to cybersecurity, including priorities, goals, and actions.
- Cybersecurity Framework (CSF): Voluntary guidance developed by NIST to help organizations manage cybersecurity risks.
- Executive Order on Improving the Nation’s Cybersecurity: Mandates federal agencies to improve their cybersecurity posture and strengthen collaboration with the private sector.
- National Cyber Incident Response Plan (NCIRP): Outlines the roles and responsibilities of federal agencies during major cybersecurity incidents.
- National Insider Threat Task Force (NITTF): Coordinates efforts to prevent and mitigate insider threats within federal agencies.
- Secure Technology Act (STA): Requires federal agencies to use secure and trusted products and services.
- Cybersecurity and Infrastructure Security Agency Training and Education (CISA T&E): Provides training and education resources for cybersecurity professionals.
- National Center for Cybersecurity and Communications (NCC): Facilitates collaboration between federal agencies, industry, and academia on cybersecurity research and development.
- Cybersecurity Workforce Framework: Outlines the skills and competencies needed for a cybersecurity workforce.
- Cybersecurity Awareness Month: National campaign to raise awareness about cybersecurity risks and best practices.
More Information
Nonpartisan Organizations
Source: Google Search + Gemini + onAir curation
- Center for Strategic and International Studies (CSIS): A bipartisan think tank that conducts research on cybersecurity issues and develops policy recommendations.
- Cybersecurity and Infrastructure Security Agency (CISA): A federal agency within the Department of Homeland Security that is responsible for coordinating cybersecurity efforts across the country.
- Federal Bureau of Investigation (FBI): The primary federal law enforcement agency responsible for investigating cybercrimes.
- National Institute of Standards and Technology (NIST): A federal agency that develops cybersecurity standards and guidelines.
- National Cybersecurity and Communications Integration Center (NCCIC): A federal agency that provides cybersecurity threat information and assistance to the public and private sectors.
- National Telecommunications and Information Administration (NTIA): A federal agency that advises the President and Congress on telecommunications and information technology issues, including cybersecurity.
- RAND Corporation: A non-profit research organization that develops solutions to public policy challenges, including cybersecurity.
- SANS Institute: A for-profit organization that provides cybersecurity training and certification.
- Security Industry Association (SIA): A trade association that represents the security industry, including cybersecurity companies.
- United States Computer Emergency Readiness Team (US-CERT): A federal agency that provides cybersecurity threat information and assistance to the public and private sectors.
Partisan Organizations
Source: Google Search + Gemini + onAir curation
Republican
- Cybersecurity and Infrastructure Security Agency (CISA): Government agency responsible for coordinating cybersecurity efforts and responding to incidents.
- House Committee on Homeland Security: Congressional committee focused on cybersecurity and threat mitigation.
- Republican Study Committee (RSC): Policy group within the House Republican Caucus that has advocated for increased cybersecurity funding and collaboration with the private sector.
- American Action Forum (AAF): Conservative think tank that supports strong cybersecurity measures while also promoting economic growth and innovation.
- Hoover Institution: Stanford University-based think tank that conducts research and advocacy on cybersecurity policy.
Democratic
- Department of Homeland Security (DHS): Cabinet-level department that includes CISA and other agencies responsible for cybersecurity.
- House Committee on Oversight and Reform: Congressional committee with jurisdiction over cybersecurity and privacy issues.
- Democratic Caucus Cyber Working Group: Subgroup within the House Democratic Caucus that addresses cybersecurity policy and legislation.
- Center for American Progress (CAP): Liberal think tank that advocates for strong cybersecurity protections and a comprehensive approach to cybersecurity challenges.
- Brookings Institution: Nonpartisan think tank that conducts research and analysis on cybersecurity and national security issues.
“Cybersecurity and Infrastructure Security Agency” (Wiki)
Contents
The Cybersecurity and Infrastructure Security Agency (CISA) is a component of the United States Department of Homeland Security (DHS) responsible for cybersecurity and infrastructure protection across all levels of government, coordinating cybersecurity programs with U.S. states, and improving the government’s cybersecurity protections against private and nation-state hackers.[4]
The agency began in 2007 as the DHS National Protection and Programs Directorate.[4][5] With the Cybersecurity and Infrastructure Security Agency Act of 2018, CISA’s footprint grew to include roles in securing elections and the census, managing National Special Security Events, and the U.S. response to the COVID-19 Pandemic.[6] It has also been involved in 5G network security and hardening the US grid against electromagnetic pulses (EMPs).[7] The Office for Bombing Prevention leads the national counter-IED effort.[8]
Currently headquartered in Arlington, Virginia, in 2025 CISA is planning to move its headquarters along with 6,500 employees to a new 10 story, 620,000 sq ft building on the consolidated DHS St. Elizabeths campus headquarters.[9]
History
The National Protection and Programs Directorate (NPPD) was formed in 2007 as a component of the United States Department of Homeland Security.[10] NPPD’s goal was to advance the Department’s national security mission by reducing and eliminating threats to U.S. critical physical and cyber infrastructure.
On November 16, 2018, President Trump signed into law the Cybersecurity and Infrastructure Security Agency Act of 2018, which elevated the mission of the former NPPD within DHS, establishing the Cybersecurity and Infrastructure Security Agency (CISA).[11] CISA is a successor agency to NPPD, and assists both other government agencies and private sector organizations in addressing cybersecurity issues.[12] Former NPPD Under-Secretary Christopher Krebs was CISA’s first Director, and former Deputy Under-Secretary Matthew Travis was its first deputy director.[13][14]
On January 22, 2019, CISA issued its first Emergency Directive (19-01: Mitigate DNS Infrastructure Tampering)[15] warning that “an active attacker is targeting government organizations” using DNS spoofing techniques to perform man-in-the-middle attacks.[16] Research group FireEye stated that “initial research suggests the actor or actors responsible have a nexus to Iran.”[17]
In 2020, CISA created a website, titled Rumor Control, to rebut disinformation associated with the 2020 United States presidential election.[18] On November 12, 2020, CISA issued a press release asserting, “There is no evidence that any voting system deleted or lost votes, changed votes, or was in any way compromised.”[19] On the same day, Director Krebs indicated that he expected to be dismissed from his post by the Trump administration.[20] Krebs was subsequently fired by President Trump on November 17, 2020[21] via tweet for his comments regarding the security of the election.[22]

On July 12, 2021, the Senate confirmed Jen Easterly by a voice vote.[23] Easterly’s nomination had been reported favorably out of Senate Committee on Homeland Security and Governmental Affairs on June 16, but a floor vote had been reportedly held (delayed) by Senator Rick Scott over broader national security concerns, until the President or Vice President had visited the southern border with Mexico.[24] Easterly hired new staff to monitor online disinformation to enhance what she called the nation’s “cognitive infrastructure” and utilized the existing rumor control website during the 2021 elections.[25]
Performance
In September 2022, CISA released their 2023–2025 CISA Strategic Plan, the first comprehensive strategy document since the agency was established in 2018.[26]
In August 2021, Easterly stated “One could argue we’re in the business of critical infrastructure, and the most critical infrastructure is our cognitive infrastructure, so building that resilience to misinformation and disinformation, I think, is incredibly important.”[27]
Recently in 2021, the Cybersecurity and Infrastructure Security Agency (CISA) released a report that provided guidance for how to navigate and prevent ransomware incidents. This was due to a significant jump in recent attacks related to ransomware.[28]
Organization

CISA divisions include the:[29]
- Cybersecurity Division
- National Cybersecurity and Communications Integration Center
- Capacity Building
- Joint Cyber Defense Collaborative
- Mission Engineering
- Office of the Technical Director
- Threat Hunting
- Vulnerability Management
- Infrastructure Security Division
- Bombing Prevention
- Chemical Security
- Exercises
- Infrastructure Assessment & Analysis
- School Safety
- Strategy, Performance & Resources
- Emergency Communications Division
- National Risk Management Center
- Integrated Operations Division
- Regions 1 through 10[30]
- Stakeholder Engagement Division
- Council Management
- International
- Sector Management
- Strategic Relations
Major Programs
The Continuous Diagnostics and Mitigations program provides cybersecurity tools and services to federal agencies.[31] [32]
CISA issues “binding operational directives” that require federal government agencies to take action against specific cybersecurity risks.[33]
In March 2021, CISA assumed control of the “.gov” top-level domain (TLD) from the General Services Administration. CISA manages the approval of domains and operates the TLD Domain Name System nameservers. In April 2021, CISA removed the fee for registering domains.[34] In January 2023, Cloudflare received a $7.2M contract to provide DNS registry and hosting services for the TLD.[35]
CISA provides incident response services to the federal executive branch and US-based entities.
CISA manages the EINSTEIN intrusion detection system to detect malicious activity on federal government agency networks.
The National Defense Authorization Act for Fiscal Year 2021 granted CISA the authority to issue administrative subpoenas in order to identify the owners of internet connected critical infrastructure related devices with specific vulnerabilities. In 2021, CISA issued 47 subpoenas.[36]
Committees
Cybersecurity Advisory Committee
In 2021, the Agency created the Cybersecurity Advisory Committee with the following members:[37]
- Steve Adler, Mayor, City of Austin, Texas
- Marene Allison, Chief Information Security Officer, Johnson & Johnson
- Lori Beer, Chief Information Officer, JPMorgan Chase
- Robert Chesney, James A. Baker III Chair in the Rule of Law and World Affairs, University of Texas School of Law
- Thomas Fanning, Chairman, President and CEO, Southern Company
- Vijaya Gadde
- Patrick D. Gallagher, Chancellor, University of Pittsburgh
- Ronald Green, Executive Vice President and Chief Security Officer, Mastercard
- Niloofar Razi Howe, Board Member, Tenable
- Kevin Mandia, Chief Executive Officer, Mandiant
- Jeff Moss, President, DEF CON Communications
- Nuala O’Connor, Senior Vice President & Chief Counsel, Digital Citizenship, Walmart
- Nicole Perlroth, Cybersecurity journalist
- Matthew Prince, Chief Executive Officer, Cloudflare
- Ted Schlein, General Partner, Kleiner Perkins; and Caufield & Byers
- Stephen Schmidt, Chief Information Security Officer, Amazon Web Services
- Suzanne Spaulding, Senior Advisor for Homeland Security, CSIS
- Alex Stamos, Partner, Krebs Stamos Group
- Kate Starbird, Associate Professor, Human Centered Design & Engineering, University of Washington
- George Stathakopoulos, Vice President of Corporate Information Security, Apple
- Alicia Tate-Nadeau (ARNG-Ret.), Director, Illinois Emergency Management Agency
- Nicole Wong, Principal, NWong Strategies
- Chris Young, Executive Vice President of Business Development, Strategy, and Ventures, Microsoft
Directors
| No. | Director | Term | |||
|---|---|---|---|---|---|
| Portrait | Name | Took office | Left office | Term length | |
| 1 | Chris C. Krebs | 16 November 2018 | 17 November 2020 | 2 years, 1 day | |
| 2 | Jen M. Easterly | 13 July 2021 | Incumbent | 2 years, 289 days | |
See also
References
- ^ “CISA Hiring Hits High Score, and We’re Not Done!!”. Retrieved 24 August 2023.
- ^ “Leadership”. US Department of Homeland Security. September 7, 2006.
- ^ “NITIN NATARAJAN”. Department of Homeland Security. February 16, 2021. Archived from the original on February 23, 2021. Retrieved April 16, 2021.
- ^ a b Cimpanu, Catalin (November 16, 2018). “Trump signs bill that creates the Cybersecurity and Infrastructure Security Agency”. ZDNet. Archived from the original on February 19, 2019. Retrieved December 16, 2018.
- ^ “About CISA”. Department of Homeland Security. 19 November 2018. Archived from the original on 6 July 2019. Retrieved 16 December 2018.
 This article incorporates text from this source, which is in the public domain.
This article incorporates text from this source, which is in the public domain. - ^ “National Risk Management Center | Cybersecurity and Infrastructure Security Agency CISA”. cisa.gov. Retrieved 2023-08-24.
- ^ “National Risk Management Center | Cybersecurity and Infrastructure Security Agency CISA”. cisa.gov. Retrieved 2023-08-24.
- ^ “OBP Fact Sheet | CISA”. cisa.gov. 2023-06-08. Retrieved 2023-08-24.
- ^ Weisner, Molly (2023-08-17). “Homeland Security to break ground on new CISA, ICE offices”. Federal Times. Retrieved 2023-08-24.
- ^ “DHS | About the National Protection and Programs Directorate”. Dhs.gov. 2011-08-26. Archived from the original on 2011-09-25. Retrieved 2011-09-27.
- ^ “Cybersecurity and Infrastructure Security Agency”. DHS.gov. Archived from the original on 23 November 2018. Retrieved 24 November 2018.
- ^ Ropek, Lucas (2020-07-28). “Will CISA Be the Savior of State and Local Cybersecurity?”. Government Technology. Retrieved 2020-11-18.
- ^ Johnson, Derek B. (2018-03-18). “NPPD taps vendor for No. 2 role”. Federal Computer Week. Archived from the original on 2019-09-30. Retrieved 2019-03-15.
- ^ Rockwell, Mark (2018-12-20). “Standing up CISA”. Federal Computer Week. Archived from the original on 2019-09-30. Retrieved 2019-03-15.
- ^ “Emergency Directive 19-01”. cyber.dhs.gov. Department of Homeland Security. 22 January 2019. Archived from the original on 3 July 2019. Retrieved 16 February 2019.
- ^ Krebs, Christopher. “Why CISA issued our first Emergency Directive”. cyber.dhs.gov. Department of Homeland Security. Archived from the original on 6 July 2019. Retrieved 16 February 2019.
- ^ Hirani, Muks; Jones, Sarah; Read, Ben. “Global DNS Hijacking Campaign: DNS Record Manipulation at Scale”. FireEye. Archived from the original on 25 June 2019. Retrieved 16 February 2019.
- ^ Courtney, Shaun; Sebenius, Alysa; Wadhams, Nick (2020-11-12). “Turmoil Hits Cyber Agency Engaged in Election as Staff Leave”. Bloomberg News. Retrieved 2020-11-18.
- ^ “Federal cybersecurity agency calls election ‘most secure in American history’“. Engadget. Retrieved 2020-11-17.
- ^ Geller, Eric; Bertrand, Natasha (2020-11-12). “Top cyber official expecting to be fired as White House frustrations hit agency protecting elections”. Politico. Retrieved 2020-11-13.
- ^ “Trump fires head of U.S. election cybersecurity who debunked conspiracy theories”. NBC News. 18 November 2020. Retrieved 2022-07-01.
- ^ Kaitlan Collins and Paul LeBlanc (18 November 2020). “Trump fires director of Homeland Security agency who had rejected President’s election conspiracy theories”. CNN. Retrieved 2020-11-18.
- ^ “PN420 – Nomination of Jen Easterly for Department of Homeland Security, 117th Congress (2021-2022)”. www.congress.gov. 2021-06-16. Retrieved 2021-07-12.
- ^ Miller, Maggie (2021-06-23). “Rick Scott blocks Senate vote on top cyber nominee until Harris visits border”. The Hill. Retrieved 2021-07-12.
- ^ Maggie Miller. (10 November 2021). “Cyber agency beefing up disinformation, misinformation team”. The Hill website Retrieved 18 December 2023.
- ^ “Strategic Plan | CISA”. cisa.gov. Retrieved 2022-09-17.
- ^ Klippenstein, Ken; Fang, Lee (October 31, 2022). “Leaked Documents Outline DHS’s Plans to Police Disinformation”. The Intercept. Retrieved 2023-01-17.
- ^ Piper, D L A (July 2021). “Cybersecurity and infrastructure security agency releases guidance regarding ransomware”. Journal of Internet Law. 25 (1): 1–17.
- ^ “Cybersecurity and Infrastructure Security Agency Divisions & Offices”. Retrieved 26 March 2023.
- ^ Cybersecurity and Infrastructure Security Agency. “CISA Regions”. Retrieved 26 March 2023.
- ^ Miller, Jason (7 November 2022). “CISA signature federal cyber program warrants more than a passing anniversary nod”. Federal News Network. Retrieved 26 March 2023.
- ^ Cybersecurity and Infrastructure Security Agency. “Continuous Diagnostics and Mitigations Program”. Retrieved 26 March 2023.
- ^ Cybersecurity and Infrastructure Security Agency (18 May 2022). “Cybersecurity Directives”. Retrieved 26 March 2023.
- ^ Cybersecurity and Infrastructure Security Agency (27 April 2021). “A new day for .gov”. Retrieved 26 March 2023.
- ^ Cloudflare (13 January 2023). “Cloudflare Wins CISA Contract for Registry and Authoritative Domain Name System (DNS) Services”. Retrieved 26 March 2023.
- ^ “CY2021 ADMINISTRATIVE SUBPOENA FOR VULNERABILITY NOTIFICATION YEAR IN REVIEW” (PDF). Retrieved 2023-06-16.
- ^ “CISA Names 23 Members to New Cybersecurity Advisory Committee | CISA”. cisa.gov. December 2021. Retrieved 2023-01-17.
External links