In the United States, border security includes the protection of ports, airports, and the country’s 3,017-mile (4,855 km) land border with Canada and 1,933-mile (3,111 km) border with Mexico. The U.S. concept of border security is deeply entwined with the persistent actual or perceived threat of terrorism, as well as more universal concerns such as immigration control, smuggling, and human trafficking. As such, the U.S. federal government is constantly reevaluating and adjusting its border security policies to reflect the perceived threats posed to the United States.
- In the ‘About’ section of this post is an overview of the issues or challenges, potential solutions, and web links. Other sections have information on relevant legislation, committees, agencies, programs in addition to information on the judiciary, nonpartisan & partisan organizations, and a wikipedia entry.
- To participate in ongoing forums, ask the post’s curators questions, and make suggestions, scroll to the ‘Discuss’ section at the bottom of each post or select the “comment” icon.
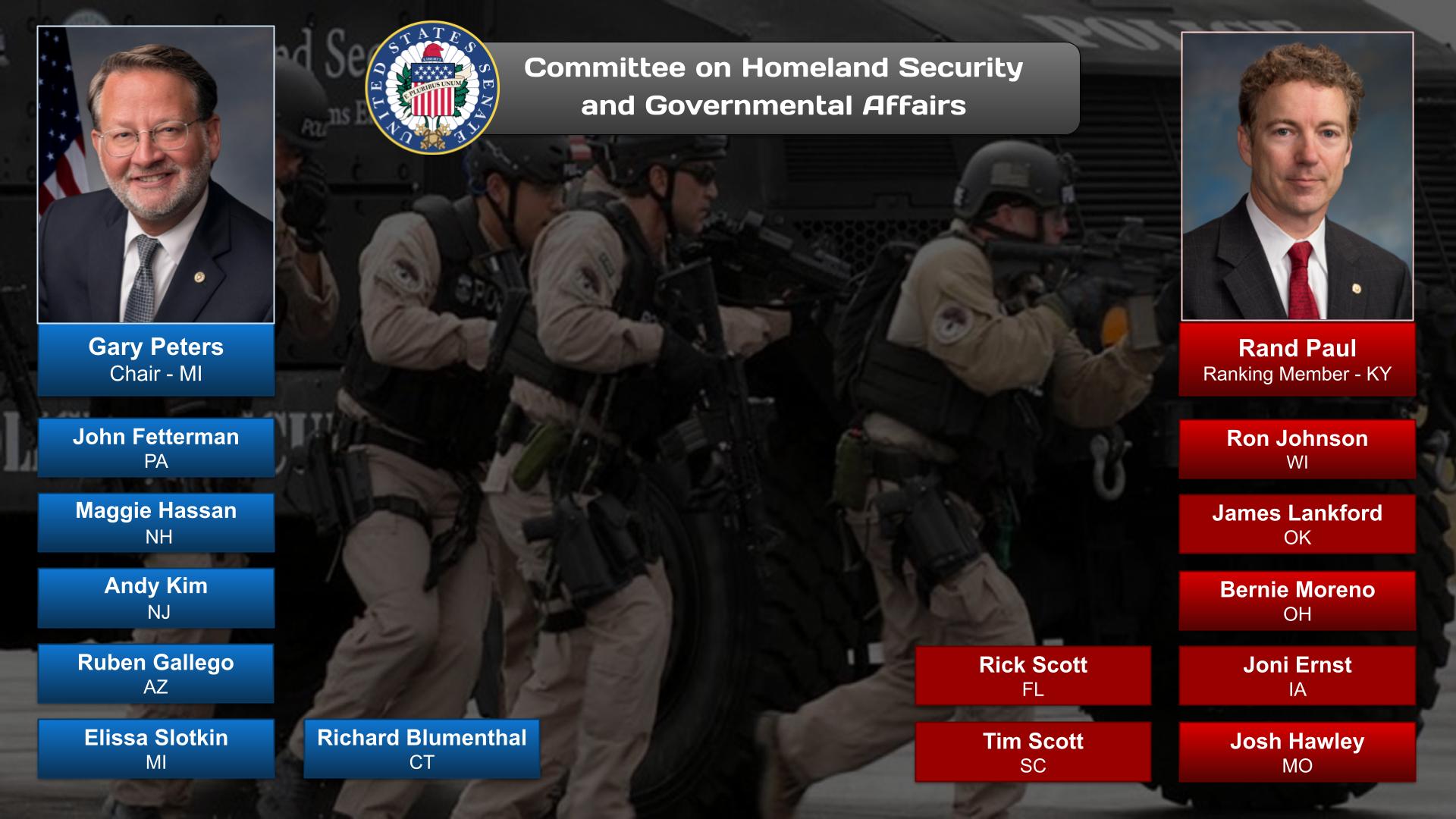
The Border Security category has related posts on government agencies and departments and committees and their Chairs.
PBS NewsHour (07:29)
https://www.youtube.com/watch?v=ZvkQb7yZlBA&t=100s
One of the most divisive issues in this year’s presidential race is immigration and border security. On the campaign trail, Vice President Kamala Harris and former President Trump have clashed over how to handle immigration policy. Lisa Desjardins takes a look at both candidates’ plans.
OnAir Post: Border Security